December 30, 2025
React Server Components Security Incident: What It Reveals About "Vibe Coding" in Production

When Vibe Coding Meets a Real CVE
Modern React and Next.js development has embraced "vibe coding." Teams build features rapidly using AI-generated snippets, starter templates, and framework defaults. They often ship to production before fully understanding complex boundaries like client-server serialization. This approach enables rapid prototyping and allows small teams to compete with larger organizations. But it carries a hidden cost: assuming "it compiles" means "it's safe" transfers unreviewed risks into production.
On December 3, 2025, the React team disclosed CVE-2025-55182, a critical vulnerability in React Server Components enabling unauthenticated remote code execution on affected servers. The issue, quickly dubbed "React2Shell," reached critical severity and prompted immediate global response. Shortly after disclosure, threat intelligence teams at Palo Alto Networks Unit 42 and Google Cloud documented active exploitation attempts. Attackers were already targeting vulnerable deployments in the wild.
This incident did not happen because teams used vibe coding. React Server Components would have been vulnerable regardless of integration approach. But the CVE exposed a dangerous reality: when production systems are built on abstractions teams don't fully understand, a single critical bug can turn "move fast and ship" into "scramble to patch before breach."
For engineering teams and technical leaders, React2Shell is a case study in what happens when development speed collides with real-world security.
React Server Components in Plain Language
React Server Components (RSC) were designed to split logic between server and client while maintaining React's component-based developer experience. Unlike traditional client-side React, RSC allows certain components to execute exclusively on the server, fetch data, run backend logic, and stream serialized output to the client. The client receives this stream, encoded in the React Flight protocol, and reconstructs the UI by merging server-rendered content with client-side interactive components.
The architecture follows a three-part pipeline:
- Server-side rendering: Executing designated components on the backend.
- Serialization: Encoding the output into the React Flight protocol (wire format).
- Reconstruction: Merging the stream into the client-side React tree.
This approach attracts fast-moving teams because it promises better performance, less JavaScript shipped to browsers, and convenient framework defaults that work out of the box. Frameworks like Next.js adopted RSC as a core feature, making it easy to enable server components without deeply understanding underlying serialization or network boundaries.
But this architecture raises the stakes. Server-client boundaries are high-risk zones where data crosses trust boundaries. Serialization, encoding complex objects into transmittable formats, has long been a notorious source of security vulnerabilities. When teams treat RSC as "just another framework feature" without understanding how server functions are exposed or how the Flight protocol handles untrusted input, they inherit risks they may never explicitly review.
What Actually Happened: React2Shell (CVE‑2025‑55182)
CVE‑2025‑55182, widely referred to as React2Shell, is a critical vulnerability in React Server Components that arises from how serialized data flowing through the React Flight protocol can be interpreted in a way that lets an attacker execute arbitrary code on the server without authentication. In practical terms, if an application used vulnerable versions of React Server Components, a remote attacker could craft malicious payloads and have those payloads processed in a way that leads to remote code execution (RCE) on the backend, turning what looks like “just” a rendering pipeline into a full server compromise. Security vendors classified this as a critical unauthenticated RCE affecting the emerging React 19 ecosystem and frameworks that adopted React Server Components, underlining that this was not a niche bug but an ecosystem-level issue. The React team’s initial advisory focused on the core RCE vulnerability, but a follow‑up post disclosed additional problems in the same area denial‑of‑service conditions and potential source code exposure showing that the attack surface around RSC and its serialization pipeline was broader than a single bug and required comprehensive patching rather than a one‑off fix.
How Fast-Moving Teams Ended Up Exposed
Most teams adopted React Server Components indirectly through framework upgrades and starter templates that enabled RSC by default, rather than designing server-client boundaries from first principles. Frameworks like Next.js integrated RSC as a core feature, allowing developers to mark components server-rendered with a simple use server directive and gain performance benefits without understanding the underlying Flight protocol or how server function endpoints are exposed. For fast-moving teams, this convenience was transformative: RSC promised better performance and cleaner data fetching without requiring deep expertise in serialization formats or runtime security models.
Why Vibe Coding Missed This
The problem emerges in the adoption pattern. Defaults and scaffolding make rapid shipping easy, but also make it easy to ship without understanding where server endpoints are exposed, how serialized payloads are processed, or what assumptions the runtime makes about untrusted input.
Teams upgrade to the latest Next.js version, copy server component patterns from docs or AI-generated snippets, run tests, and deploy, often without auditing React versions in production or reviewing security advisories for newly adopted features.
When engineers rely on templates, auto-generated code, and the "it passes tests, ship it" mentality, especially under deadline pressure, they inherit complex behaviors they may never explicitly review. React2Shell exploited exactly this gap: the vulnerability lived in serialization logic most teams never touched directly but inherited through framework dependencies. The incident revealed that treating RSC as "just another framework feature" without understanding its security-critical boundaries can turn convenient abstractions into production liabilities the moment a critical CVE surfaces.
The Real Risks of Vibe Coding in Production Environments
Security Risk: CVE-2025-55182 enabled unauthenticated remote code execution, allowing attackers to run arbitrary commands on vulnerable servers, the most severe vulnerability class in a widely adopted ecosystem.
Exploitation Risk: Threat intelligence teams at Palo Alto Networks Unit 42 and Google Cloud reported active exploitation attempts shortly after disclosure, turning a theoretical bug into a live threat against internet-facing applications.
Operational Risk: Organizations faced urgent pressure to triage affected services, patch vulnerable React versions, deploy mitigations, and monitor for compromise often across dozens of services under tight timelines.
Organizational Risk:
Teams treating RSC as "just a framework feature" without understanding its security model experienced slower, more chaotic incident response, exposing the gap between development speed and security readiness.
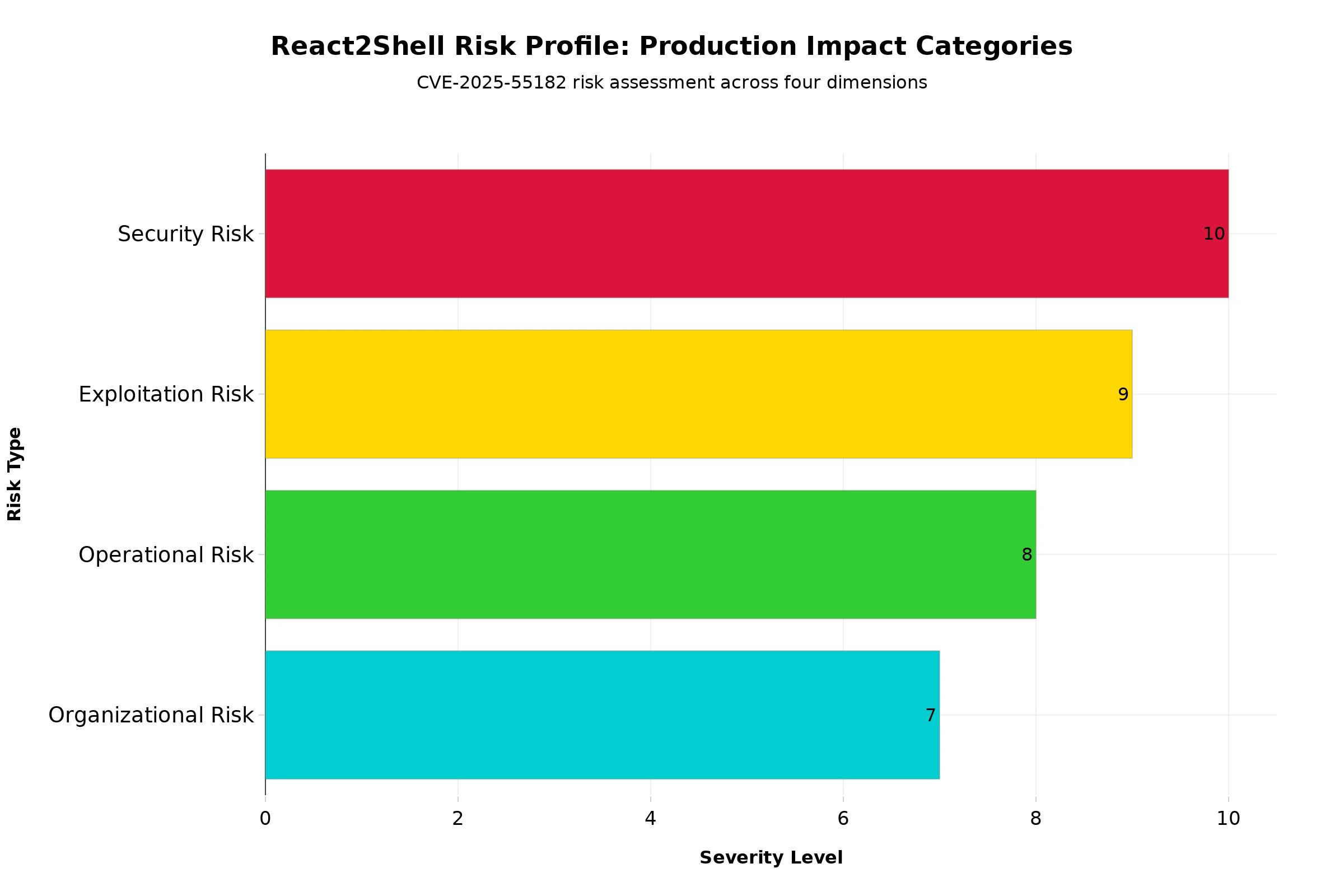
Figure 1: React2Shell risk profile showing the severity of four production impact categories, from critical security vulnerability to organizational readiness gaps
A Realistic Scenario: A Vibe-Coded Feature Under Fire
The following is a fictional but plausible scenario based on documented exploitation patterns and vulnerability characteristics described in official advisories and threat intelligence reports.
Phase 1: November 2025 – Shipping at Speed
A product team at a mid-sized SaaS company ships a new customer dashboard built on Next.js 14 with React Server Components enabled by default. The team moves fast, copying server component patterns from official docs, using AI-generated snippets to scaffold data-fetching logic, and relying on starter templates pre-configured with RSC.
Security reviews focus on authentication at the route level, but no one audits how the React Flight protocol handles serialized payloads or where server function endpoints are exposed. The team assumes the framework has "handled security."
Phase 2: December 3, 2025 – Disclosure Day
The React team discloses CVE-2025-55182, a critical unauthenticated remote code execution vulnerability in React Server Components. Within 24 hours, proof-of-concept exploits circulate online.
Phase 3: December 5, 2025 – Active Exploitation Begins
Automated scanners and threat actors begin targeting exposed RSC endpoints across the internet. The company's monitoring systems detect unusual traffic patterns hitting their customer dashboard.
Threat intelligence from Palo Alto Networks Unit 42 and Google Cloud confirms active exploitation campaigns in the wild. Engineers discover they're running React 19.0.0, a vulnerable version with exposed server function endpoints.
Phase 4: Emergency Response
The team faces crisis mode: patch to a safe version, deploy mitigations, audit logs for compromise, and verify no attackers achieved code execution.
The core problem surfaces immediately. No one fully understands how RSC serialization works, where Flight protocol endpoints are exposed, or what successful exploitation looks like in logs. They scramble to read security analyses, reverse-engineer their deployment, and coordinate emergency patches across services while trying to learn internals of a system they shipped without fully studying.
The incident becomes a case study in how "move fast and ship" collides with an operational crisis when critical CVEs turn theoretical risk into reality.
What Production Teams Should Actually Do Now
1. Follow Official Remediation Guidance
Upgrade or downgrade React and affected frameworks immediately according to official React advisories treat these as non-optional security patches. For teams running React 19.0.0 through 19.0.0-rc-65a56d0e-20241020, patching to safe versions eliminates the vulnerability at its source.
2. Use Security Vendors' Playbooks
Apply mitigations from security researchers at Rapid7, Wiz, and Palo Alto Networks Unit 42: narrow exposed server function endpoints, deploy WAF rules to detect malicious Flight protocol payloads, and monitor for suspicious patterns linked to CVE-2025-55182. These interim protections are critical for teams needing defense-in-depth while verifying patches across all services.
3. Integrate Threat Intelligence Into Engineering
Treat advisories from Unit 42 and Google Cloud Threat Intelligence as regular engineering inputs, not just security-team concerns. When threat-intel teams report active exploitation campaigns, engineers should respond within hours, subscribe to vendor security feeds, monitor CISA's Known Exploited Vulnerabilities catalog, and establish clear escalation paths.
4. Raise the Bar for Vibe Coding in Production
Keep using vibe coding for prototypes and experiments, but require an explicit review step before production: dependency inventory, understanding of server-client boundaries, and checks for known advisories affecting new features. This checkpoint ensures "move fast" doesn't mean "ship blind."
Keeping the Speed, Adding Discipline
React Server Components did not break because teams used vibe coding; the vulnerability existed in serialization logic regardless of integration approach. But the incident exposed how fragile it is to rely on frameworks and generated code without understanding underlying behavior and security assumptions. For developers and technical leaders, React2Shell is a case study in balancing speed with discipline. Keep vibe coding's productivity benefits for rapid prototyping and competitive velocity, but pair that speed with disciplined practices: maintain architecture awareness, read security advisories for tools you depend on, and treat patching as core engineering responsibility. The gap between "it compiles" and "it's secure" requires intentional management. Teams that shipped RSC without understanding Flight protocol serialization or version-specific vulnerabilities learned this when CVE-2025-55182 turned abstractions into overnight liabilities. Moving forward, build engineering cultures where speed and security awareness coexist where "move fast" pairs with "know what you shipped" as a non-negotiable standard.
References:
- React (official) Critical Security Vulnerability in React Server Components
- React (official) Denial of Service and Source Code Exposure in React Server Components
- Rapid7 React2Shell (CVE-2025-55182): Critical unauthenticated RCE affecting React Server Components
- Palo Alto Networks Unit 42 Exploitation of Critical Vulnerability in React Server Components (and related Next.js issue)
- Wiz React2Shell (CVE-2025-55182): Critical React Vulnerability
- Google Cloud Threat Intelligence Threat actors exploit React2Shell (CVE-2025-55182)